Recursive Organizations Takeover through the Invitation Flow

During a bug bounty activity in a private program, my teammate Mekkawy and I discovered and exploited this critical flaw through the invitation process.
Summary
The application implements an organization-based model where each user can join multiple organizations. Each organization is a fully isolated environment with its subdomain and authentication system.
The organization admin can issue an administrative access token, which can be used to perform privileged operations (e.g., managing users, modifying settings, etc.) on that specified organization (as it is said :D).
During our testing, we identified a flaw in the invitation process that leads to full compromising of the victim’s organizations.
The scenario can be summarized at some points:
- Hijacking invited users using only the invitation ID, without needing the invitation token.
- Getting into the victim’s account but in the isolated attacker organization without the ability to access the other victim organizations (which seems to be useless)
- Generating an organization access token as the victim user to the attacker’s organization.
- Exploit a misconfiguration in the organization access token that allows us to access victim’s organizations invitations.
This leads to full compromise of unrelated victim organizations, including the ability to list and reuse additional invitation IDs to escalate further.
Vulnerability Chain
First stage: Insecure Invitation Flow
- Admins invite users, and a secure email link is sent to the victim that includes a strong invitation Token
https://attacker.target.com/user/invitations/{invitationToken}- However, the response to the invite request discloses an invitation ID.
- Visiting the invitation endpoint but using the invitation ID, immediately logs into the attacker organization as the invited victim — no interaction, no token, no consent required.
https://attacker.target.com/user/invitations/{invitation_id}After spending over three days thoroughly analyzing the application, we aimed to identify another vulnerability to chain with a critical impact.
Gaining Access to Victim’s Organizations through a Misconfiguration in the Organization Access Token
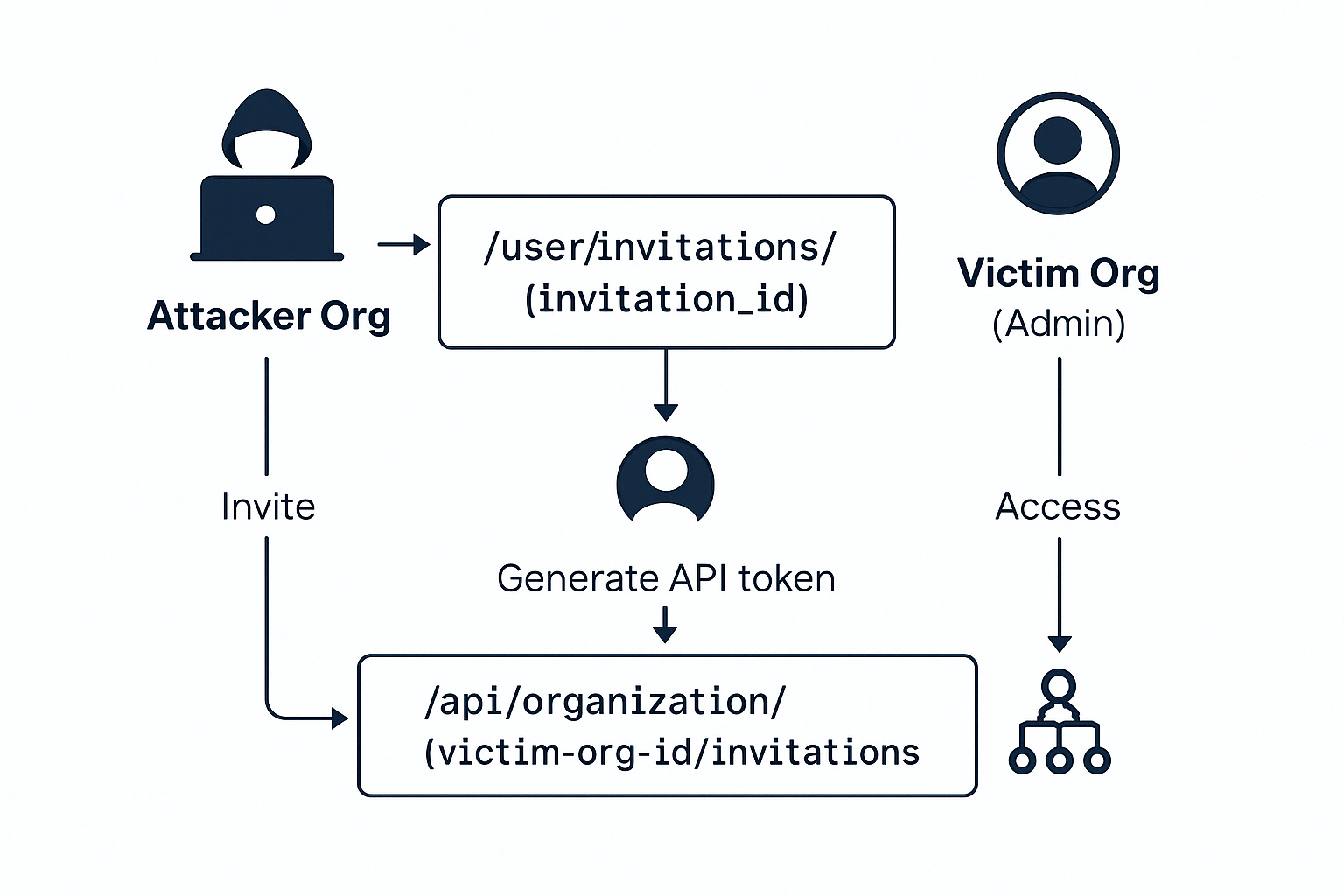
- The attacker invites a victim who is an admin in another organization.
- Exploit the invitation flaw to hijack this victim invitation and log in as the victim to the isolated attacker’s organization.
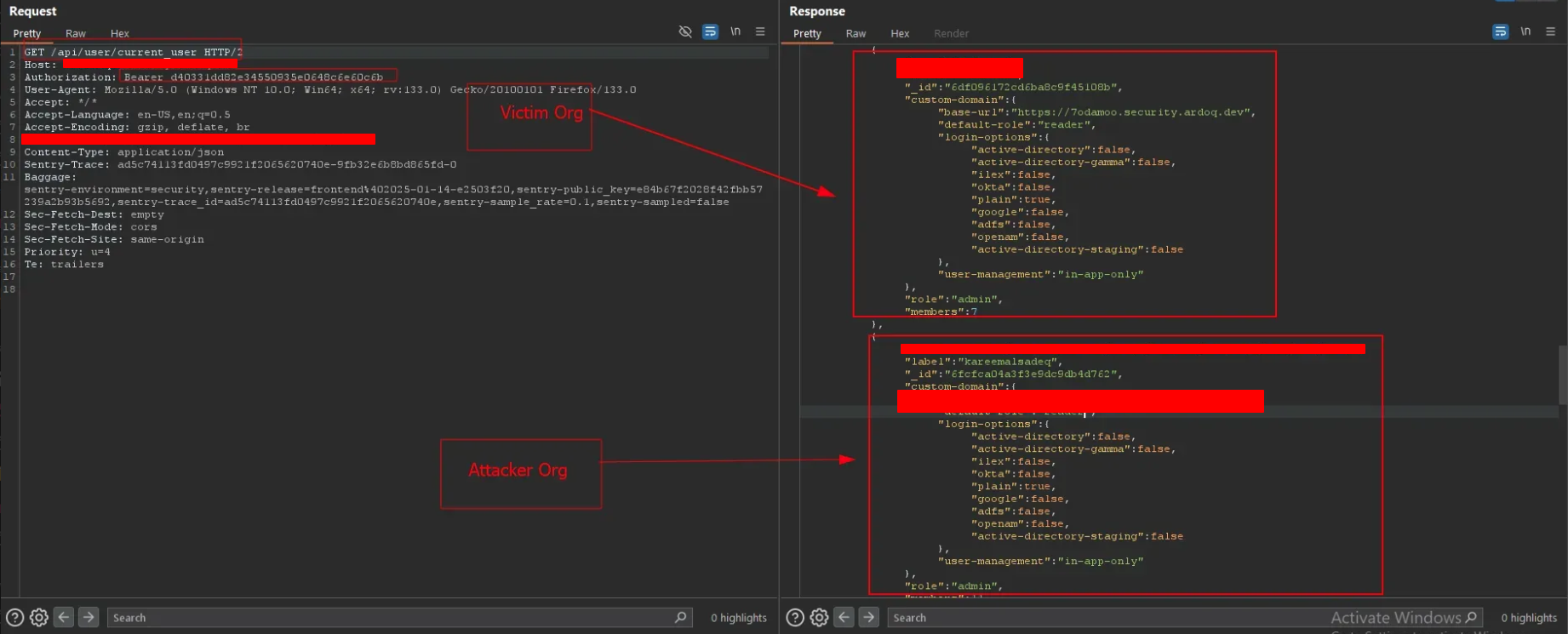
- Generate an organization access token from the victim’s account, which should be specified to the attacker organization.
- Exploit the token misconfiguration: The token allows cross-organization access to any organization where the victim is an admin, not just the attacker's one.
- Get the victim's organization ID with the generated token
- The attacker can now pick any invitation from the victim organization and repeat the same invitation hijacking attack scenario, such as:
https://victim.target.com/user/invitations/<victim-invitation-id>" - This allows complete hijack of additional users and further escalations with different privileges and maybe with different organizations:
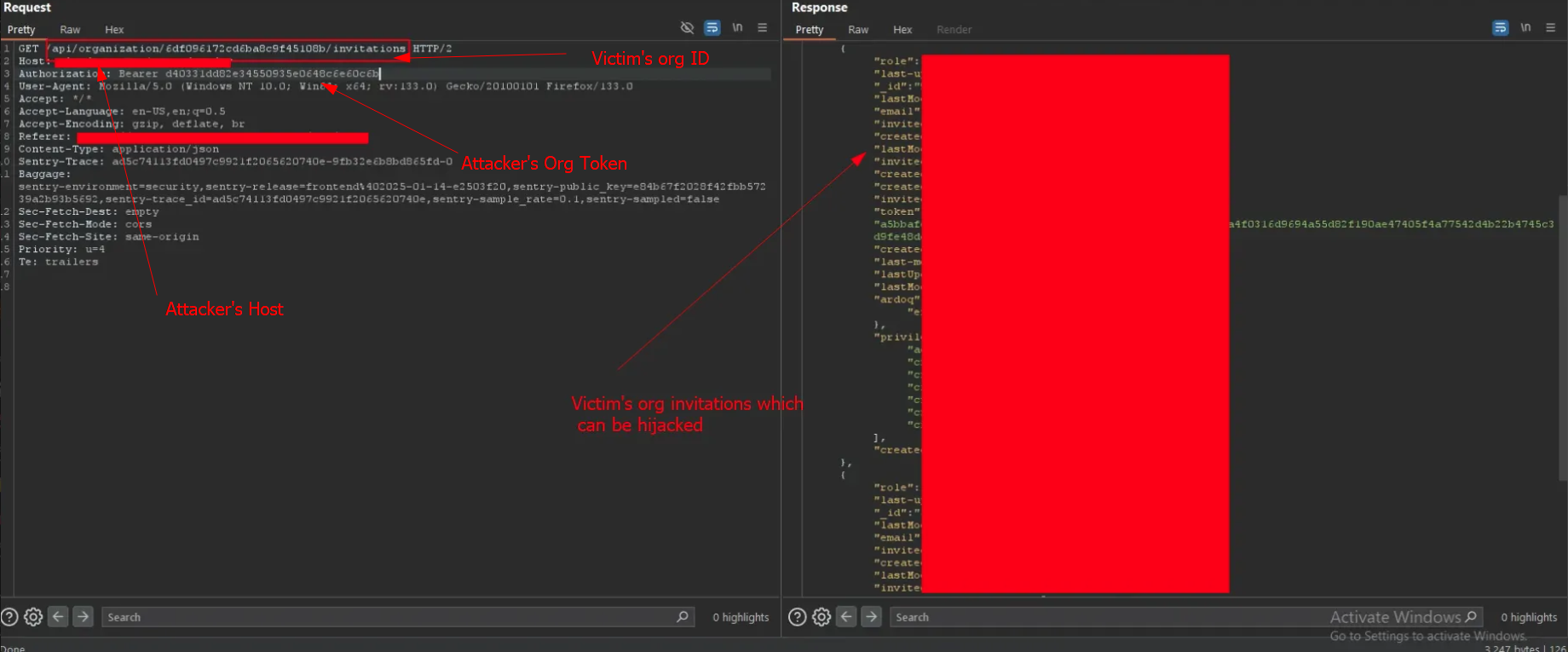
Victim Invitation Hijacking >> Exploit Organization Token Misc >> Recursively hijacking the Victim's Organization users